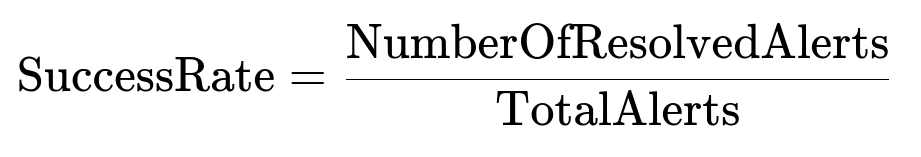ML Case-study Interview Question: Automated Code Vulnerability Fixing Using LLMs and Static Analysis Integration
Browse all the ML Case-Studies here.
Case-Study question
An enterprise has thousands of repositories with frequent security vulnerabilities. They built a system that uses an internal code scanning engine to detect potential security alerts and calls a large language model to generate automated fixes. They integrated these fixes into their pull request workflow so developers can review or edit the suggestions before merging. As a Senior Data Scientist, design this end-to-end pipeline. Explain how you would detect vulnerabilities, generate valid fixes, handle language-specific contexts, ensure high precision, validate correctness with tests, minimize model error, and measure success. Outline your solution approach, technical rationale, and how you would scale and monitor this system in production.
In-depth solution
The core approach ties static analysis with large language model suggestions for code fixes. Static analysis is used to discover vulnerabilities and gather the relevant code context. That output is fed to an LLM-based fix generator that returns suggested patches. Post-processing cleans and validates these patches to ensure correctness and avoid syntax errors.
Detection of vulnerabilities
Use a code scanning engine to detect potential security flaws in different languages. Include data-flow analysis to identify untrusted inputs propagating into sensitive sinks. Store alert data (file paths, line numbers, flow paths) in a structured format.
Prompt construction
Assemble a minimal but sufficient code snippet around each alert location. Combine problem descriptions with relevant lines to give the LLM enough context. Restrict LLM edits to these lines by explicitly telling the model not to modify code outside them.
Model output format
Specify a strict output schema. Request:
A natural language explanation of the fix.
A clear patch specification.
Optional extra dependencies.
Post-processing
Parse the LLM output. Align the “before” blocks with the original code via a fuzzy match if line numbers are off. Apply fixes to a temporary branch. Run syntax checks and static type checks if available. Fail early if these checks do not pass. If a new dependency is suggested, confirm it is valid and safe.
Validation with tests
Run the repository’s test suite on the temporary branch. Re-run the static analysis to ensure the original alert is resolved and no new alerts appear. Fix suggestions that pass these checks can be offered to developers in pull requests.
Success metrics
Use an automated test harness. For each alert with test coverage, generate a patch, commit it on a fork, then run tests and re-scan.
NumberOfResolvedAlerts is the count of alerts successfully eliminated without introducing new ones. TotalAlerts is the total count of alert instances processed.
Infrastructure
Embed the fix-generation step in the code scanning pipeline. When a pull request triggers a scan, the service calls the LLM, filters results, and returns suggestions as diff patches. Cache repeated queries to lower resource usage. Store only aggregated usage metrics, not raw user code.
Monitoring
Track aggregated system metrics (fix acceptance ratio, average LLM response time, test suite pass rate, error logs). Check for surges of partial or failed suggestions. Alert on abnormal spikes in fix rejections or anomalies in pipeline latency.
How would you handle code from multiple languages?
A multi-language solution means hooking static analyzers for each supported language. Each analyzer yields structured alerts. The fix generator’s prompt must differ by language, specifying language-specific fix strategies. One approach is to keep a modular architecture with language-specific heuristics to handle library imports, dependency management, and syntax differences.
What if line numbers from the model output do not match actual code lines?
Implement fuzzy matching on the “before” code blocks. Search the repository file for a close match, allowing for differences in whitespace or comments. If mismatches are too large and cannot be resolved heuristically, discard or re-request a fix.
How do you manage false positives and ensure minimal developer friction?
Use robust code scanning queries that produce fewer noisy alerts. Provide an edit button so developers can tweak fixes. If the user dismisses too many suggestions, investigate those queries. Continuously refine query rules and fix prompts. Track ratio of accepted vs. dismissed fixes and improve accordingly.
How do you ensure generated fixes do not introduce new security issues?
Run the same static analysis after applying the fix. Verify no new alerts appear. Conduct syntax checks, type checks, and confirm the fix adheres to best practices. If any suspicious or unauthorized library calls are introduced, reject the patch. Rely on an internal or third-party vulnerability registry to guard against malicious package dependencies.
How would you scale and optimize the LLM calls?
Batch alerts in a single request if possible. Cache repeated queries by storing a hash of prompt text and reusing prior suggestions when identical patterns recur. Monitor request-response latency. If usage grows, move to more efficient model instances or prompt-tuning. Reduce extraneous code in the prompt to minimize token usage and cost.