ML Interview Q Series: How would you build a bomb-flagging system, covering inputs, outputs, accuracy evaluation, and testing?
📚 Browse the full ML Interview series here.
Comprehensive Explanation
Designing a robust detection model for identifying potential bombs at a border crossing involves careful consideration of how data is gathered, represented, and processed, as well as how the model is trained, validated, and deployed. A key aspect is ensuring that the model emphasizes safety (minimizing false negatives) while also balancing the need to reduce false alarms. Below is a detailed breakdown of the main considerations.
Structuring the Model’s Inputs
When detecting something as critical as bombs, the inputs often need to be diverse and potentially multimodal. Various sensor data sources might be relevant:
Visual Scans Using standard or high-resolution cameras or X-ray images that capture suitcases, luggage, or cargo from multiple angles. Preprocessing might include segmentation, color normalization, or background subtraction. Radiation or Chemical Sensor Data If specialized hardware can detect unusual radiation or chemical traces, these signals could be incorporated. Typical preprocessing might involve normalizing sensor readings to account for ambient variation. Metal Detector or Magnetometer Signals Data from advanced metal detectors might be used to detect large masses of metal or unusual densities. Textual or Categorical Information You may have extra metadata, such as traveler history or cargo type. These additional features could be encoded as categorical variables or embeddings.
Structuring the Model’s Outputs
A common approach is a binary classification output, typically a probability value for “bomb detected” vs. “no bomb.” However, for a system that could have severe consequences if it misses something dangerous, it might be prudent to produce more granular outputs or multiple categories. For instance:
Probability of Threat The model could output a continuous value from 0 to 1, representing the likelihood of an item being a bomb. This allows for dynamic thresholding. Categorical Labels The system might not only produce “bomb” vs. “no bomb” but also highlight specific categories of suspicious items, such as “chemical explosive,” “metal-based IED,” or “unknown suspicious object.” Attention or Highlight Regions In computer-vision-based approaches, attention maps or bounding boxes might be generated to indicate where the model sees something suspicious. This helps human operators double-check the flagged regions.
Measuring Accuracy and Evaluation
For safety-critical scenarios, overall accuracy is often insufficient because the costs of different types of errors vary widely. A single false negative might lead to disastrous consequences, while a high false positive rate might cause operational bottlenecks. Therefore, we typically measure several metrics:
Sensitivity/Recall This measures how many of the actual bombs (positive cases) the model detects. Formally, it is:
where TP is true positives, FN is false negatives.
Maximizing recall reduces the chance of missing a real bomb. In a border-crossing context, recall is extremely important because failing to catch a real bomb can be catastrophic.
Specificity/True Negative Rate This considers how many non-bomb cases are correctly identified. It might be crucial for operational efficiency: an overly sensitive model that flags everything as suspicious could cause major delays.
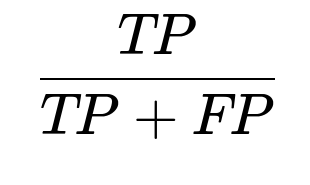
Precision This is another important metric:
where FP is false positives.
In a high-volume setting such as border crossings, having a low-precision model will overwhelm the system with false alarms.
F1 Score The harmonic mean of precision and recall:
F1 is helpful when you need a single measure that accounts for both false negatives and false positives. In many bomb-detection contexts, recall is prioritized over precision, but F1 is still a good overall reference point.
Testing the Model
Rigorous testing is critical. It involves real-world simulation, continuous updates, and environment-specific trials to ensure robust performance under various conditions.
Simulation and Synthetic Data In the event that real bomb data is hard to obtain, simulation might be used to generate realistic images or sensor readings of bombs. This is useful for data augmentation. Cross-Validation on Historical Data Where feasible, data from past scans that include known contraband or bombs can be split into training, validation, and test sets. Field Trials and A/B Testing Eventually, the model might be tested in a real or closely simulated border checkpoint environment. Gradual rollout can help validate performance and gather feedback without risking immediate widespread deployment. Monitor Model Drift Over time, new threats or new ways to conceal bombs might appear. Continual monitoring ensures that the model is updated and retrained to handle these evolving tactics.
Practical Example with a Simple Classifier
Below is a very simplified example in Python using a convolutional neural network (CNN) for image-based detection (e.g., from X-ray scans). This example focuses on typical steps and leaves out complexities like advanced data augmentations or multi-modal inputs.
import torch
import torch.nn as nn
import torch.optim as optim
from torch.utils.data import DataLoader
class SimpleCNN(nn.Module):
def __init__(self):
super(SimpleCNN, self).__init__()
self.conv1 = nn.Conv2d(3, 16, kernel_size=3, padding=1)
self.conv2 = nn.Conv2d(16, 32, kernel_size=3, padding=1)
self.fc1 = nn.Linear(32*8*8, 128)
self.fc2 = nn.Linear(128, 1)
self.relu = nn.ReLU()
self.pool = nn.MaxPool2d(kernel_size=2)
def forward(self, x):
x = self.relu(self.conv1(x))
x = self.pool(x)
x = self.relu(self.conv2(x))
x = self.pool(x)
x = x.view(x.size(0), -1)
x = self.relu(self.fc1(x))
x = torch.sigmoid(self.fc2(x)) # Probability of bomb
return x
# Hypothetical dataset and loader
# train_dataset: (images of cargo, label indicating bomb/no bomb)
train_loader = DataLoader(train_dataset, batch_size=32, shuffle=True)
model = SimpleCNN()
criterion = nn.BCELoss() # Binary Cross Entropy for 0/1 classification
optimizer = optim.Adam(model.parameters(), lr=1e-4)
for epoch in range(10):
model.train()
for images, labels in train_loader:
optimizer.zero_grad()
outputs = model(images)
loss = criterion(outputs.squeeze(), labels.float())
loss.backward()
optimizer.step()
# Evaluate on a validation or test set
# Collect predictions, compare with ground truth, and compute metrics like recall, precision.
In a real system, you might incorporate more complex networks, augmented data from multiple sensor types, and advanced hyperparameter tuning.
Follow-Up Questions
How would you handle class imbalance when bombs are extremely rare?
Class imbalance is almost guaranteed because genuine bomb instances are exceedingly infrequent. One approach is to use class weighting in the loss function, emphasizing the minority class. Another is oversampling the positive class or undersampling the negative class. Synthetic data generation (for instance, simulating bombs in X-ray images) can also help augment the minority class. It is crucial to monitor metrics such as recall, because a naive model can ignore the minority class altogether and still achieve high overall accuracy.
What steps would you take to minimize false negatives?
Minimizing false negatives is often the top priority. Techniques include:
Raising Detection Threshold If the output is a probability, lower the threshold for flagging suspicious items, thus reducing missed detections. Utilizing Ensemble Methods Combining multiple models trained on different data subsets or with different architectures can produce a more robust decision boundary. Continuous Monitoring and Retraining If new types of threats emerge, retraining with the latest data ensures that the model remains up to date. Human-In-The-Loop Verification Potentially suspicious cases flagged by the model could receive additional inspection by trained personnel to ensure minimal risk of letting a true threat pass.
How can you deploy this model and keep it updated?
A continuous integration/continuous deployment (CI/CD) pipeline is ideal:
Regular Data Collection Gather labeled data from daily operations and incorporate relevant new suspicious items into the training set. Retrain or Fine-Tune the Model on a Schedule If the distribution of threats shifts (e.g., new bomb designs), the model must adapt quickly. Edge Devices vs. Cloud Processing Decide whether to run inference at the border crossing in real time (edge device deployment) or rely on cloud-based servers. Edge deployments might require model compression or optimization for speed.
How do you address adversarial attempts to fool the model?
An adversary might deliberately try to circumvent detection by altering the appearance or composition of bombs. Strategies include:
Adversarial Training Exposing the model to examples that mimic adversarial modifications (e.g., new shapes, metal distributions, or concealed appearances). Physical Robustness Testing Checking model reliability against distortions such as noise, rotation, occlusion, or partial visibility. Explainable AI Tools Methods like Grad-CAM or saliency maps can help inspectors understand which parts of an image the model is using to make a decision. If suspiciously small or irrelevant regions are highlighted, the model might be vulnerable to adversarial manipulation.
How would you ensure the system works in real time at a busy border?
Efficiency can be critical. Possible solutions include:
Model Pruning and Quantization Reduce model size to improve inference speed, especially in resource-constrained environments. Approximate or Lightweight Architectures Instead of massive deep networks, specialized architectures like MobileNet or efficient CNN architectures can maintain performance with lower latency. Batch Processing or Parallel Scans If hardware permits, images or sensor data can be processed in parallel to keep up with throughput demands.
How would you handle missing or incomplete sensor data?
In real deployments, sensors may fail or produce incomplete readings. Potential strategies:
Data Imputation If only some sensor channels are missing, a learned imputation model can approximate them from other available channels. Graceful Degradation The system might default to a less confident classification using the remaining sensors and raise a flag for manual inspection if the missing data is critical. Redundant Sensors Using multiple devices that capture overlapping information lowers the risk of a single point of failure.
Overall, designing a bomb detection model for border crossings demands thorough planning on how to gather and preprocess data, structure the outputs, and define success metrics that align with stringent safety requirements. Testing must be ongoing and should mirror realistic conditions as closely as possible. Proper handling of extreme class imbalance, adversarial tactics, and deployment constraints further ensures that the system can operate reliably and securely in a high-stakes environment.
Below are additional follow-up questions
How do you ensure interpretable model outputs so human inspectors can verify suspicious regions quickly?
Interpretability is crucial in high-stakes environments like bomb detection, where trust in the model’s conclusions can save lives. One approach is to use methods such as Grad-CAM, Integrated Gradients, or SHAP to highlight which portions of an image or which sensor readings most influenced the model’s classification. This is especially useful when human operators need to confirm whether a flagged region really contains a suspicious object.
A subtle issue arises when the model’s most activated regions consistently fall outside the actual suspicious area, which could imply it is “cheating” based on irrelevant factors (e.g., color patterns, backgrounds). This pitfall can lead to overfitting on non-threat-related image artifacts. Thorough testing—where bounding-box annotations or region-of-interest ground truth are available—can reveal when the model’s explanations align poorly with the actual threat objects, prompting retraining or architecture revisions.
What if the scanning hardware or sensor type gets upgraded or changed?
Sensor or hardware changes can shift the data distribution significantly, even if the underlying labels remain the same. For instance, a new generation X-ray scanner might produce sharper images with different contrast levels, or a newly installed sensor might capture a different range of chemical signatures.
One practical approach is domain adaptation: you can collect parallel data from old and new scanners to train a transfer model that aligns both feature spaces. Another strategy is to leverage unsupervised domain adaptation if labeled data from the new hardware is initially scarce. A pitfall is assuming the model will continue to perform well across hardware changes without explicit domain adaptation. If not addressed, performance can degrade unpredictably.
How would you handle extremely large-scale images or scans with many items?
In real-world scenarios, a single X-ray or camera scan can contain multiple items, each requiring analysis. A naive approach might scale down the image significantly, potentially losing critical detail about small compartments where explosives could be hidden.
A common solution is to employ a detection or instance-segmentation model (e.g., Faster R-CNN, YOLO, or Mask R-CNN) that identifies bounding boxes or masks for each object. The system can then classify each object within the bounding box. One potential edge case occurs when the items overlap or have complex shapes that do not fit neatly into bounding boxes. In such cases, segmentation-based methods that delineate object boundaries might be needed to avoid misclassifying items that are partially hidden behind others.
Additionally, if there are very dense scans (e.g., cargo containers with hundreds of objects), the model might experience extremely long inference times. Techniques like sliding-window or tiling can help break images into manageable chunks, although you must ensure that suspicious objects are not inadvertently cut across tile boundaries.
How do you handle data augmentation specifically for bomb detection tasks?
Data augmentation can help address class imbalance and improve generalization. For bomb detection, you might insert simulated bomb-like objects into benign scans or synthetically add noise, distortions, or occlusions that emulate real-world conditions (e.g., baggage stacked on top of each other). Another augmentation might involve randomizing the shape or materials of suspicious items, so the model doesn’t overfit to a narrow subset of bomb designs.
However, a pitfall is over-augmentation with unrealistic or anatomically impossible alterations. For instance, if bombs are pasted into images at bizarre angles or with mismatched textures, the model might learn artifacts instead of genuine features. Balancing realism and variation is key. You may also need to carefully track how these synthetic examples affect the model’s recall and precision on genuine examples.
How do you address ethical and privacy concerns when collecting data for training?
Collecting high-resolution scans of personal belongings could reveal sensitive information about travelers. There may also be restricted data on actual bomb cases. To handle these issues, strict data governance policies are needed. This can involve anonymizing data—removing or obscuring personally identifiable details—and encrypting all stored scans. Additionally, implementing a well-defined data retention policy ensures that irrelevant historical data is purged in a timely manner.
One hidden pitfall arises if you store entire scans indefinitely in an unprotected environment, exposing travelers’ possessions or personal details to data breaches. Another subtle challenge is ensuring that any shared dataset among research institutions or external contractors includes only the minimal set of necessary features. Over-collection of data for convenience can raise both privacy and compliance concerns under regulations like GDPR.
What if you need to adapt the same model for multiple threat categories, not just bombs?
In many real scenarios, you want to detect various threats such as firearms, knives, or other contraband. An expanded approach transforms the output layer from binary classification (bomb vs. no bomb) to a multi-class or multi-label setup. Each threat category can get its own probability or classification node.
A key pitfall is that training a single model for too many categories might cause confusion or degrade performance for certain classes if there’s insufficient data for each threat type. Class imbalance can become more pronounced across multiple categories. Another subtlety is that certain items (e.g., chemicals) might overlap categories (e.g., harmless chemical vs. explosive), making labeling trickier. Evaluating the trade-off between a unified multi-threat model versus specialized per-threat models can be critical.
How would you calibrate the probability outputs to handle risk-based decisions?
In practice, the raw probabilities from a model might not reflect true event likelihoods. Calibrating these outputs allows you to set thresholds that correspond to real-world risk appetites. Techniques like Platt scaling (fitting a logistic curve) or isotonic regression can align model outputs with actual observed probabilities.
If calibration is off, a threshold that was believed to yield, for example, a 5% false positive rate might in reality yield a 20% false positive rate, causing operational chaos. Conversely, if the system is underestimating the risk, critical threats could go unnoticed. To avoid this, you need a well-structured calibration set and continuous monitoring to detect calibration drift over time, especially as bomb-making techniques evolve or scanning hardware changes.
How can you manage a multi-country or large-scale deployment with different legal standards and operational protocols?
Different countries may have varying regulations about how data is collected, stored, and shared. They may also impose distinct operational procedures for responding to flagged items, which could affect how or when the model’s output is acted upon. For instance, one jurisdiction might allow immediate enforcement actions solely based on model output, while another requires a human operator to verify a suspicious item.
This means you might end up with multiple models or configurations per region—some with stricter thresholds, some with more robust privacy features, or different feature sets. A subtle pitfall is incorrectly assuming that a model trained for one country’s scanning procedures and cultural contexts will work identically in another. For instance, the types of luggage or packaging materials commonly used might differ, altering the distribution of normal vs. suspicious data. Thorough local testing and possibly region-specific fine-tuning become essential.
What if real-world data contains many “confounding” suspicious items that are not bombs, like batteries or camera lenses?
Common objects in luggage, such as external battery packs, camera equipment, or large metal tools, might resemble bomb components to less sophisticated models. This increases false positives. One strategy is to annotate these frequent confounders in training data. By explicitly training the model on “common but not dangerous” items, it learns to differentiate them from actual threats.
A potential pitfall occurs if you do not adequately capture the variation of these confounders. For example, new camera lenses or battery designs might show up that the model has never seen, causing a spike in false positives. To mitigate this, continuous retraining with new data that includes the latest consumer goods or cargo items can keep the model up to date.
How do you retrain with limited new bomb data but plenty of normal scans?
Genuine bomb data often remains scarce, and new variations may be discovered sporadically. You might consider leveraging transfer learning or few-shot learning approaches. In transfer learning, a model might be first pre-trained on a large dataset of regular objects, learning generic feature extraction. Only the final layers are then fine-tuned on the limited bomb-related data.
One subtlety is ensuring that the model doesn’t forget previously learned detection of older bomb types (catastrophic forgetting). Using knowledge distillation or maintaining a small curated set of previous bomb examples can preserve historical knowledge. Another approach is to systematically generate synthetic bombs based on real designs, though realism is paramount to ensure the model learns meaningful features and not just synthetic artifacts.
What if you need to handle dynamic environmental changes like extreme weather or power fluctuations that affect sensor reliability?
Sensors under harsh environmental conditions—very hot or cold climates, high humidity, dust—might produce noisier or partial signals. In practice, the model might begin to fail or degrade in unexpected ways if the distribution of sensor data shifts beyond its training distribution.
One strategy is to actively monitor sensor quality. If the sensor feed is flagged as “degraded,” the system can either switch to a fallback rule-based approach or prompt immediate manual inspection. You might also train a domain-invariant representation that remains robust across multiple environmental conditions. A pitfall here is ignoring the possibility that at certain extremes (e.g., abrupt power surges), the data might be utterly unusable, requiring a system-level fail-safe rather than relying on model-based decisions.
How do you handle potential sabotage of the data-collection or labeling process itself?
An adversary might try to corrupt training data by injecting misleading labels or synthetic scans. For instance, if you crowdsource some portion of labeling or rely on automated labeling pipelines, an attacker could deliberately mislabel suspicious items as benign.
Robust data ingestion pipelines and verification procedures are essential. This can include random spot-checking of labels, cross-validation by different labeling teams, or automated anomaly detection on incoming data (e.g., looking for suspicious patterns where a certain subset of suspicious samples gets systematically mislabeled). A hidden pitfall is relying exclusively on a single labeling channel—once compromised, the entire dataset may become unreliable. Dual or triple redundancy in labeling, especially for the most critical classes, can mitigate this risk.